The Anatomy of a Ransomware Attack
According to PurpleSec, the business impact due to ransomware attacks is estimated to be $20B in 2020, up from $11.5B in 2019, with the average cost per ransomware attack tagged at $133,000. While there has been a tremendous amount of press whenever an organization suffers a ransomware cyberattack, there is very little information provided as to exactly HOW a ransomware attack happens.
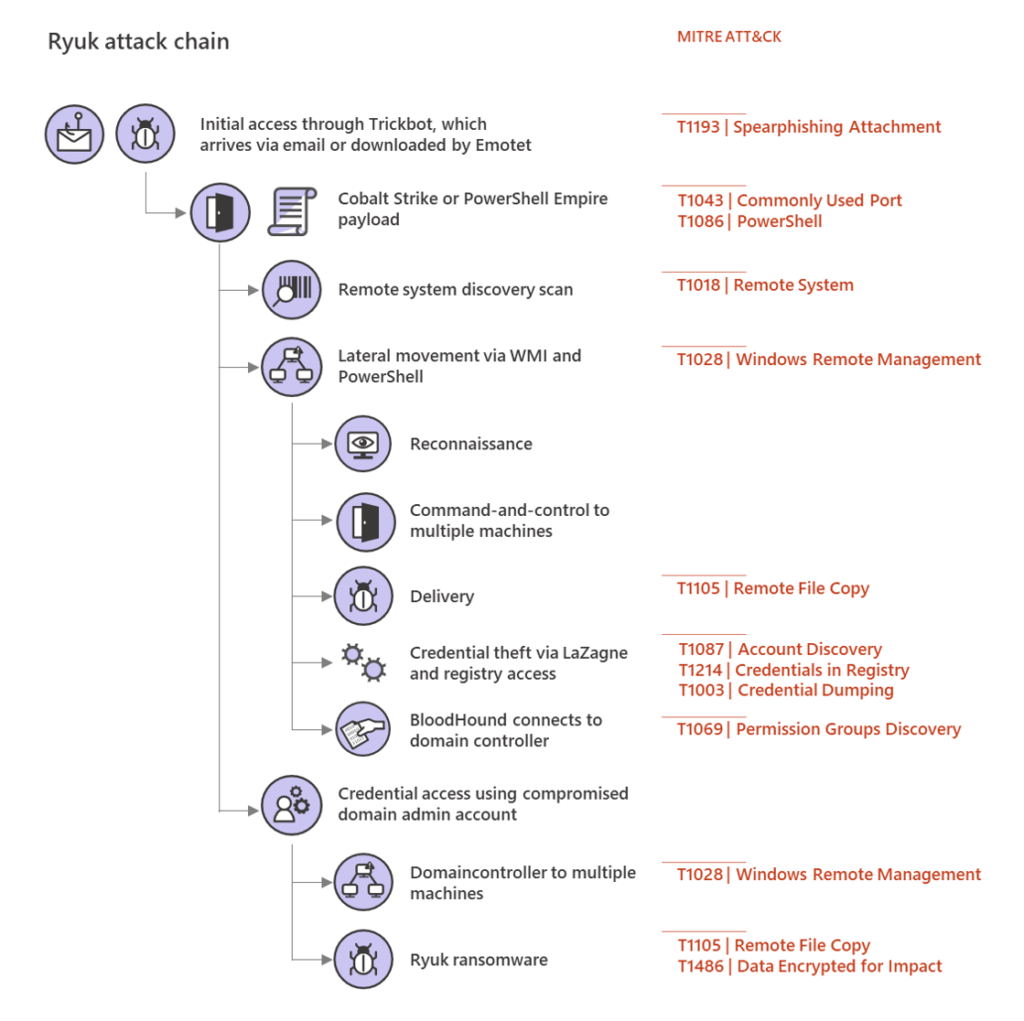
As shown the above diagram of the Ryuk ransomware strain, this attack starts by either brute force guessing account credentials via a public Remote Desktop endpoint, or the deployment of a TrickBot malware application via an end-user opening an Email and clicking on a malicious link or attachment. Once the TrickBot is installed, this runs via the context of the account credentials of the end-user (typically Domain User, and does not have Domain Admin rights).
The TrickBot then installs various other malware tools that permit the attacker to directly interact with the infected desktop, which allows the attacker to then move laterally throughout the corporate network to other desktop computers and corporate network servers. During this step, the attacker implements a process called "Pass the Hash" (PtH), which obtains the password hash of accounts that have logged into the attacked machine. The goal of this malware step is for the attacker to gain the password hash of a Domain Administrator which, once obtained, gives the attacker full access to complete the exfiltration and then encryption of all organization data (electronic documents, databases, etc).
This PtH process is completed by malware applications querying the various Microsoft Windows authentication systems, such as the Local Security Authority Subsystem Service (lsass.exe) and the Security Account Manager (SAM) database. These are used by the Windows operating system to provide single sign-on functionality, which caches the account credentials when someone logs onto a system. Access to these security systems happens constantly by any application that is initiated by a user process, so at any given point in time there are a significant number of valid authentication requests to LSASS and SAM.
The key is to identify if/when a malicious request to the Windows authentication system occurs, and immediately alert the administration team and terminate that process request. This differs tremendously by the current anti-virus vendors that look for file signatures of malware for detection, which by definition fails to detect "zero-day" attacks. By contrast, by developing a process that monitors for these malicious access requests and immediately terminates the request, we will "cut off the oxygen" of these ransomware attacks from happening.
Stay tuned to this blog or subscribe to our newsletter here if you would like to stay aware of advancements in this area.
